Phishing : don’t get caught in the scammers net
Now more than ever, we need to be aware of scammers and their persistent attempts to steal our passwords. The most common method for this is known as Phishing, and if you are not familiar with this concept then you need to read this article in full. Even if you are of aware of it, this can serve as a useful reminder during this time of the COVID-19 pandemic, when scammers are more active than ever.
Posing as recognised organisations in order to obtain our personal data, scam emails have become increasingly sophisticated and quite difficult to distinguish from genuine messages. Plus, these fraudsters don’t lack imagination. Anything from bank notices, to COVID-19 donations, HMRC refunds and TV licences. But, there are tell-tale errors that allow us to protect ourselves by taking the appropriate action.
Below we provide a guide on what to look out for and what to do if you accidentally drop your guard. But, before we do, we would like to let you know some good news. An effective tool already exists to protect you from almost all Phishing scams.
Multi-Factor Authentication (MFA or 2FA)
Phishing scams are largely operated for the purpose of gathering username and password information for cloud services from unsuspecting computer users. MFA adds a secondary passcode to an online service issued to your mobile (by text message) or smartphone (by app) meaning you are less exposed if you do get phished. Even with your login name and password, scammers would also need your phone (and the one-time code) to access your account. All services accessible on the Internet now have this feature and it is usually a very simple process to activate it with your mobile device.
Seek out and enable MFA features for all your online services!Now onto how to spot a Phishing scam. Learn and use the following checklist to evaluate email messages that just don’t look right and it could save you a lot of trouble in the long run.
1. Poor Spelling and Grammar
Let’s start with a common tell-tale sign – the grammar.
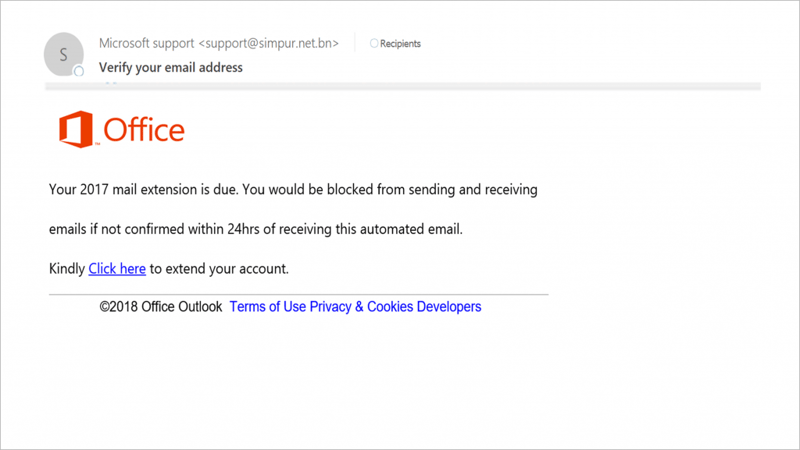
Established and trustworthy companies want to maintain a certain reputation, and spelling mistakes are sure to hurt their image. If the message includes clumsy use of language or poor punctuation, you probably have yourself a scammer.
If it’s written perfectly, which is unlikely, keep an eye out for inconsistent text styles and sizes or mismatching logos. Scammers aren’t experts at email layouts, they’re experts at stealing.
2. Fake Email Addresses
They may be experts, but they can’t lie about where they’re sending the email from. Look closely at the sender email and keep an eye out for anything suspicious.
No reputable company will send you an email from a personal address (e.g. hotmail.com, gmail.com, icloud.com). Anything that doesn’t end with the company name in the domain, which is the part after the ‘@’, is not a legitimate email.
And yet, the smarter scammers don’t even use personal emails. Their favourite tactic is using a variant of a legitimate company name. All it takes is a quick switch of the letters and your brain might not immediately notice the difference.
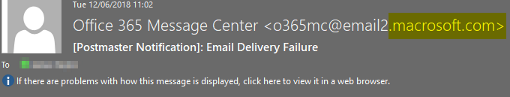
So if you’re receiving an email from “macrosoft” instead of “microsoft”, that’s clear evidence of deceit.
If you have doubts regarding the domain name of a company, all it takes is a quick online search and you’ll have your answer.
3. Be Suspicious
As if it wasn’t hard enough, scammers will even use legitimate email business addresses, where they can. The first thing a scammer will do after they acquire mailbox login credentials and scanning the contents, (usually if that mailbox has little chance of being used for financial gain) is to launch from it a fresh batch of phishing messages in an attempt gain access to more useful mailboxes (people with positions of financial responsibility).
These can be hardest phishing emails to detect because they seemingly come from legitimate, business email systems and, sometimes, even from people you do business with. You best defence against this type of fraud is to be suspicious of all message that do not follow usual business process, include unusual requests or demands and have strict internal procedures around financial transactions e.g. do not accept bank account change information over, use a two-tier approval process (phone & email) for payments above a certain value.
4. Hover, Don’t Click
In the hustle and bustle of daily life, the first thing that comes to mind might not be to check the email or search online. Especially if the email is short, was sent by somebody you don’t usually correspond with or it comes with an attachment.
If there isn’t enough information in an email and the only instruction is to click the link or download a file to find out what it’s about, you might be tempted just go ahead and click it. The message below is a common example. This message alerts the recipient that they have received a voicemail message with a link to retrieve it. Hovering over the link reveals a suspicious address:
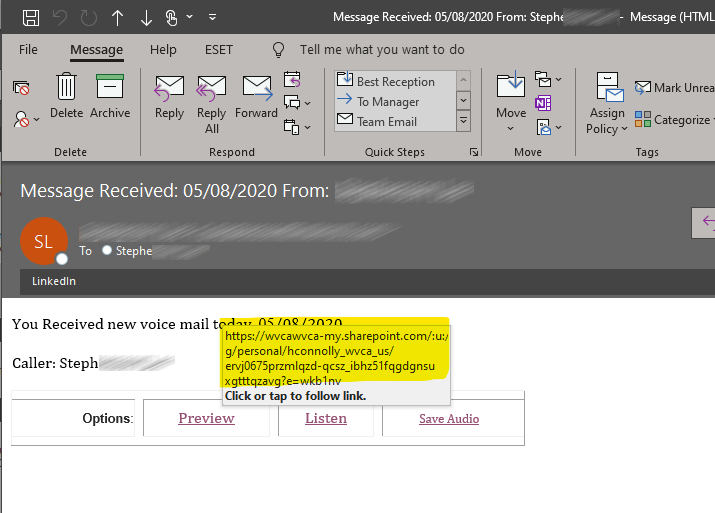
This link could lead to one of the following:
- There’s malicious code in the link and you’ve activated some malware, which will be hard to avoid especially if you’re running outdated applications.
- It directs you to a website that asks for your personal information
- It directs you to a fake sign-on page for a cloud service designed to capture your password
Of course, it’s better to avoid them all – but how? Luckily, it’s pretty simple. Instead of clicking the link immediately, which is an urge that you might have to train yourself to ignore, hover over it with your cursor. If the link looks suspicious or is completely different from the company name and website, don’t click it.
This may be a bit less linear on a mobile phone, but there’s still a solution. You can check the real link by holding it down with your finger and waiting for the bubble to pop up. Inside the bubble, you’ll find the option to display the full URL of the destination and… voila! The truth is revealed.
As for the attachments – it’s better to be safe than sorry. Don’t download them. If anything, find a way to contact the sender and ask for a further explanation.
5. Impersonal Greetings
“Dear Client…”
In the age of data-driven marketing, you would think that the company would have your first AND last name by now. Yes, some scammers are moving on to including your first name in the greeting, but few go to the trouble.
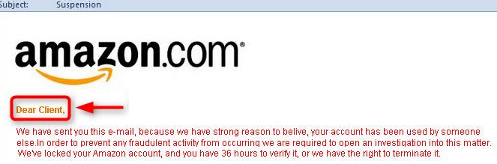
Look out for the simple “Hi” or “Hello/Dear [Your email address]” and think about all the times you’ve received incredibly personalised emails from legit companies.
6. Urgency and Deadlines
Urgency is a psychological trigger that pushes us to take action quickly, particularly if it’s from someone in a position of authority.
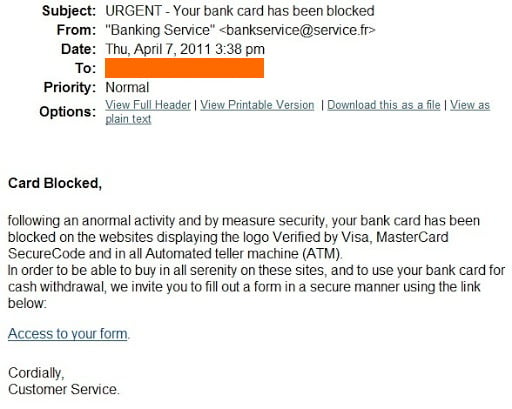 Scammers know this and capitalise on it by including urgent tones and messages. Of course, their aim is to have you click their links immediately than give you the time to figure out it’s a scam.
Scammers know this and capitalise on it by including urgent tones and messages. Of course, their aim is to have you click their links immediately than give you the time to figure out it’s a scam.
If you receive such an urgent message, don’t give in to the fear. If the email is asking you to do something you feel uncomfortable about or is giving you incredibly tight deadlines, think before you leap. And yes, that goes for what looks like internal company emails too! Your management team would much rather you check than compromise company security.
7. Personal Information
“We will never ask for your account number, password, or any other personal information in an email.”
Have you read this anywhere before? This is what companies include in their emails to make sure you don’t fall for phishing scams. If the email is asking for your PIN number or personal identification information, it’s best to let it go.
8. Check With The Company
If you’ve completed the checklist and are still not sure, it might be time to contact the sender.
Contact the company and find out if the email is genuine or not. Organisations that are aware of circulating scams regularly publish advice on what to watch out for and how to avoid them.
What to do if You Click on a Phishing Link
Ok, so you were distracted and clicked on a phishing link – now what? Alert your IT department or Managed Service Provider in the first instance, of you have one. If not, don’t panic, just follow some steps to make sure you mitigate the damage.
You clicked a link to a fake website:
- Do NOT enter your data or login details.
- If you did enter password information, sign into the real online service and change that password immediately
- If you entered financial information, contact the institution immediately and follow their guidelines
You clicked a link that appears to have launched a suspicious program:
In this case, by the time you get to the infected website, the damage may already be done.
- Disconnect your computer from the internet immediately. You can contain the malware infection by unplugging the network cable or switching off the network connection on your device.
- Scan your machine using a reputable, updated anti-virus/anti-malware software using the full-scan mode.
- Remember to remain disconnected from the Internet until the scan is complete and shows your computer to be clean.
Education & Awareness
Even though adding Multi-factor Authentication to online services provides an excellent level of protection against Phishing scams, the scammers are adapting all the time. The vulnerability that they exploit is almost always a human one, so it in order to provide a complete defence against online scams, it is worthwhile to include training into the mix.
Combining technical measures with staff that are alert and aware is a fraudsters nightmare, so consider running workshops to discuss common scam practices or improve business processes to identify weaknesses. It is even recommend to run simulated scam attacks on your own business to both raise awareness and find flaws in your processes and procedures. Proactive measures like these could save a fortune in the long run!
Summary
If you have read down this far and you are feeling somewhat anxious and confused, fear not. We understand that it can feel like a bit of a minefield and some of the guidelines, such as inspecting links, may seem quite complicated for the non-technical computer user. Simply follow these summary guidelines and you will be on the right path.
- Enable Multi-Factor (Two-factor) Authentication on ALL online accounts as standard
- Suspicion is good. Phishing relies on human curiosity to be successful. If something doesn’t look right, do not take action and always double-check.
- Use reputable, updated protection software on your computer
- Create clear and strict policies in your organisation around the processing of financial transactions and limit the use of email in them
- Circulate regular reminders to staff or run training programs to raise awareness
As always, ITbuilder is here to help and advise. If you would like to discuss any aspects of this article, please get in touch via the contact details in the top menu or leave a comment below.
James Naylor
James Naylor is ITbuilder's Managing Director and Founder. He has worked in technology since the early nineties and, after a decade in the corporate world, went into business himself.
James has lead ITbuilder for over two decades, building the business into the force that it is today, but is still a technician at heart and still very hands on with tech.
Despite growing up in Hertfordshire, James lives in the Netherlands for five years as well as London, before returning and setting up the base in Hertford, where he lives today.
More articles from James Naylor

